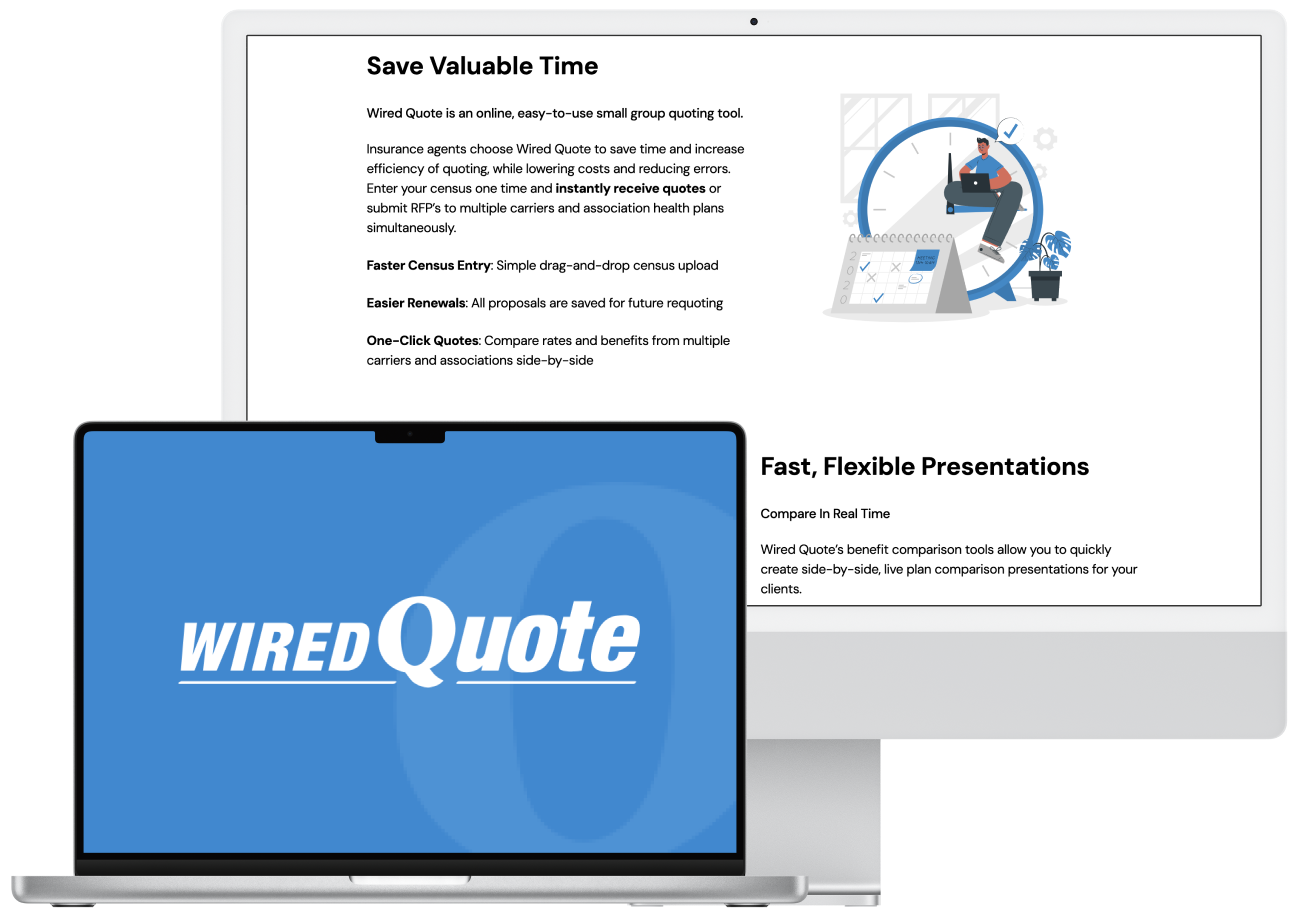
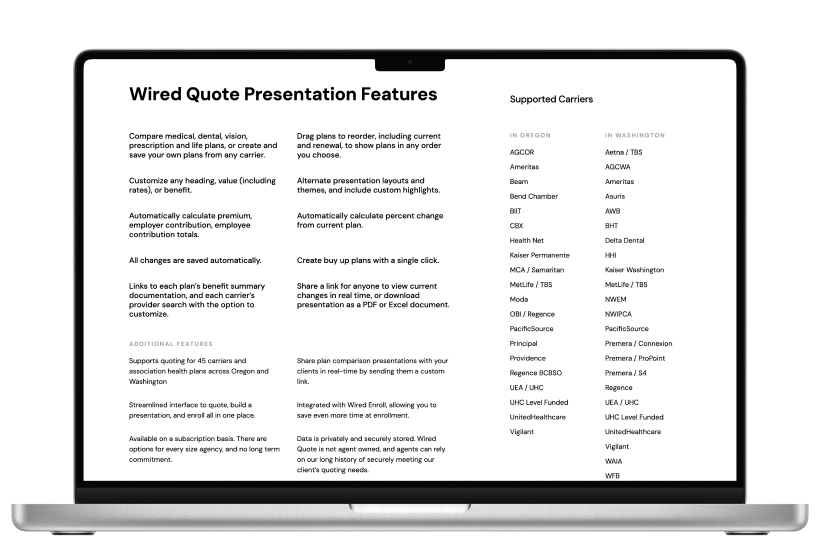
To reach the primary goal of the project, our team identified application-based threats to vulnerabilities in the application, compared WiredQuote current security measures with industry best practices, provided recommendations that WiredQuote can implement to mitigate threats and vulnerabilities and meet industry best practices.
DICEUS provided web app penetration testing services that included the following tests: application security testing, bypassing security controls like Intrusion prevention systems (IPS and WAF), testing for the latest OWASP Top 10 and SANS25 security risks (SQL-injections, XSS, SSRF, XXE, etc.), testing REST API security implementations and misconfigurations according to the OWASP API Top 10, unauthenticated and Authenticated testing, access control matrix verification, testing for vertical and horizontal privileges escalation, bypassing multi-tenancy security controls, and more.
We provided the client with a penetration testing report and remediation report including a summary of business risks, high-level recommendations, and findings details.