What we offer
The digital world is constantly threatened by cyber-attacks where criminals are never tired of trying to breach the security armor of software and infrastructure to access vulnerable or financial data of companies and individuals. Penetration testing as a service (aka pentest as a service) that we provide aims at exposing vulnerabilities of applications and other solutions, networks, databases, etc., and thus enhancing cybersecurity within your organization. The pentesting services we render embrace the following aspects.
Vulnerability check
Having ordered pen testing as a service, the management of your company gets an accurate external and internal evaluation of all endpoints, devices, servers, and software pieces located on-premises or in the cloud. This procedure, which is conducted via both authenticated and non-authenticated techniques, is called to step up your risk management policy and augment the overall security of the organization’s systems and resources. As a result, you are left with insights that serve as guidelines for your decision-making.
Ethical hacking tests
Our team of seasoned pen test service providers performs a legitimate attack on your company’s web resources and solutions utilizing the most advanced and sophisticated methods contemporary hackers leverage. The deliverables of this process include an actionable account of the discoveries, an exploitation report, and recommended steps to address the pinpointed issues.
Security testing
Since mobile and web apps are the most widely used types of software, penetration testing as a service should focus on them especially. Therefore, we thoroughly analyze apps of any kind that your enterprise relies on in its workflow, emphasizing secure coding and vulnerability detection.
Forensic analysis
Modern security testing as a service expands into related domains and covers data forensics. Our investigators employ advanced system searches, decryption, reverse engineering, and other cutting-edge methodologies to identify an accident’s root cause and influence. In addition, they utilize the best practices in the field and a chain of custody to store the obtained evidence.
Social engineering
In the post-COVID world, many organizations switch to remote mode in their shopfloor activities, and this type of access should also be secure. We check the defenses of your systems via the simulation of real-world attacks through remote access. Such testing scenarios embrace the most common email phishing attacks and other methods which consider your company’s specifics.
Cybersecurity training
The pentest service nowadays can’t be called comprehensive without penetration testing service providers training customer personnel. They must be aware of this sector’s relevant security threats and trends. So, we not only educate the staff along these lines but also instruct them on the basics of software security development.
Cyber security is one of the top concerns of any digitally-driven business of the early third millennium. Pentesting as a service is essentially honed to expose vulnerabilities of the cyber environment and prevent any data leakages and system compromise. Alongside this primary goal, penetration testing is instrumental in establishing and/or fine-tuning the organization’s security policies, augmenting employees’ security awareness, and gauging the company’s readiness and ability to identify and handle security challenges and threats.
Our specialists engaged in pen test services have the necessary skills and experience to conduct exhaustive authenticated and non-authenticated testing procedures and detect inadequacies or even gaps in the cyber shield of your organization that hackers may exploit. They will see that these shortcomings are disposed of and that your company’s cyber-attack protection meets all modern requirements to resist penetration attempts.
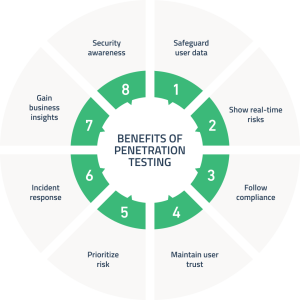
Benefits of penetration testing
Digital technologies are a bedrock of the lion’s share of contemporary businesses, and this reliance will only grow in the foreseeable future. However, the seamless functioning of IT-powered organizations is impossible if they aren’t fully protected from the malevolent activity of cybercriminals. Upgrading such protection is possible via penetration testing as a service that ushers the following boons.
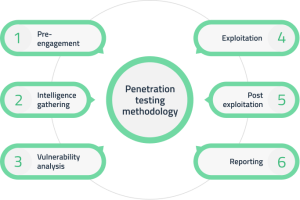
Our penetration testing process
Having conducted dozens of penetration tests, we have come up with a clear and straightforward roadmap that aims to guarantee the procedure’s efficiency and is based on flexible cooperation.
What impacts your project duration
The time that the complete penetration testing of your resources and systems will take is conditioned by such factors.
- Project requirements
- Scheduled deadlines
- Team roster
- Selected platform and tech stack
- The complexity of test cases
What affects your project costs
One can’t give the precise sum you must allocate unless the following aspects are known.
- Urgency of completion
- Applied technology
- Project complexity and scope
- The chosen engagement model (Dedicated Team, Time and Material)
- The time testing takes
What we need from your side
Penetration testing is a two-way street that requires the close cooperation of all stakeholders. To accomplish it swiftly and efficiently, we need our customers to provide the following information:
- Project vision, objectives, and roadmap (in case it exists)
- Detailed project requirements
- Project-related documentation like software architecture or mockups (if available)
- Expected deadlines
- Customer accessibility (several hours for weekly requirements sessions)
Our tech stack





























































Explore our case studies
Frequently asked questions
What are the penetration testing stages?
Penetration testing consists of several stages. At first, the testing team gathers all the information they will need for the procedure. Then, the systems are scanned for loopholes and vulnerabilities, which are shortlisted for exploitation. Next, testers connect with the target by performing typical security attacks (SQL injection, DoS attack, session hijacking, etc.). The access is maintained for a long time to maximize the infiltration. After this, all obtained data are gathered, and a detailed report is prepared. Finally, all traces of the simulated penetration are removed to prevent real-world hackers from using them as a gateway into the system.
What are the top 5 penetration testing techniques?
Today, ethical hackers make use of five basic methods. During external testing, the visible assets of a company (the website, email server, web and mobile apps, etc.) are checked. Internal testing aims to imitate an attack on resources protected by the firewall. In blind testing, experts know only the name of the organization they will check. In the process of double-blind testing, the customer’s employees aren’t informed of the simulated attack their systems will undergo. By contrast, testers and the organization’s personnel cooperate closely during targeted testing.
What are the main aims of penetration testing?
Ethical hackers perform a simulated cyber-attack on an organization’s hardware and software resources to tap existing inadequacies in the protection mechanisms and expose all vulnerabilities. Alongside enhancing cyber protection of the digital environment, penetration testing helps improve the company’s cyber security policies and increase the personnel’s security awareness.