Easy to follow tips on securing your data warehouse
Which factors do you consider the most threatening for a business? Financial risks? Competitors? Disruptive technologies? Surely, these aspects are important but cybersecurity issues remain the most dangerous and devastating. Grasp the number: 1.76 billion personal records were leaked in January 2019 alone! Costs of hacker attacks count in billions of dollars while the global cost approaches several trillion. No enterprise can feel safe now, so DWH privacy matters.
We realize how essential data warehouse security is. Working with banks and insurance companies, our developers have to design flawless systems to protect business and customer-sensitive data. In this guide, we share the knowledge gathered over the years of experience. You will learn about privacy basics and challenges, ways to improve your data warehouse protection, including encryption methods and hardware-based approaches.
Read more:
How to implement a DWH for bank
Understanding DWH privacy
A data warehouse or DWH is a software tool that collects business information from several sources. Put simply, it’s a repository. It stores data, provides quick access and helps in the analysis. Obviously, it also must be safe. And here comes the main problem.
In a nutshell, DWH privacy is similar to this aspect in other systems. Protected apps should prevent unauthorized access and hacker attacks while employees should be able to get the required data when they need it. However, too strict access would interfere with users working with the information seamlessly. Moreover, security always affects performance.
Business owners should care about the protection of the company’s/users’ data before building databases. Pay attention to the ways you’re going to use the data. For instance, warehouses focused on selling data should feature separated access levels for each client. Simultaneously, bases for internal work should prioritize quick and error-free processes.
Crucial security challenges for warehouses
Let’s look at the current issues of data warehouse modeling and protection. Apart from the aforementioned importance of balancing between smooth access and security measures, there are a few other points:
- Classification tasks: how to define the user clusters to provide them correct access. This point may include employees only or add customers and partners, too.
- Encryption methods: it’s all about tech things. Managers should get the best software/hardware combination to keep low costs and set high quality.
- Extraction question: databases not only store info but allow users to view it, exchange, upload, and download it. Security measures should consider these weak links.
- Performance influence: the more complicated and protected a system is, the more resources it requires. Heavy loads lead to crashes and, potentially, other leaks.
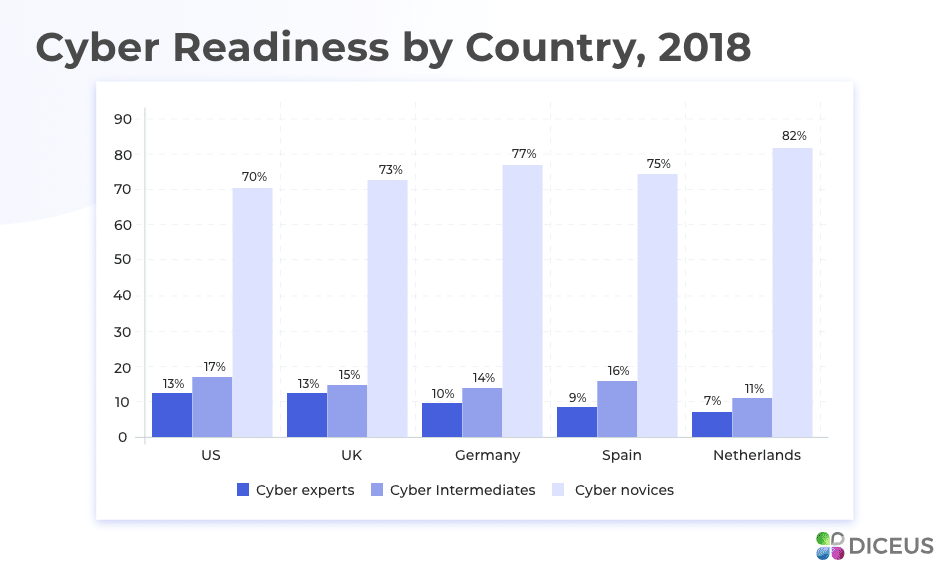
In 2018, in the report published by Hiscox, researchers surveyed more than 4,000 companies from the USA, the UK, Spain, Netherlands, and Germany. The results revealed that 73% of companies aren’t ready for hacker attacks at all, i.e. they were so-called «cyber novices». To deal with the listed challenges and become at least a «cyber intermediate», businesses should start with the architecture of the planned system.
Data warehouse architecture aspects
Just trust us: it’s much easier to build a robust and protected platform than to redesign it to get better DWH privacy, add new features or upgrade security layers later. Naturally, enterprises grow by acquiring new clients or partners. This process leads to new data sources, as well as new access levels. Without proper initial planning, you will have to add security measures and set access for all the new partners, spending extra resources.
Hence, let’s think about how to build a reliable database at the beginning. According to data warehouse modeling, there are four key activities to remember.
1. User accesses
To start with, there’s a system of access layers. They can be set based on different criteria, e.g. data types, job functions, the company’s hierarchy or employees’ roles. When you design the warehouse, you should think about data people will access and then classify both information and end-users.
There are two data classification approaches:
- Sensitivity-based. Highly-sensitive personal information will be more restricted while generic data will be available to more users.
- Function-based. Specific user categories will be able to access only the data they need for their work. Other information will be blocked.
And two user classification methods:
- Hierarchy-based. This model is suitable for enterprises with few departments. Thus, you can create data marts with unique accesses for each team.
- Role-based. If a company has a lot of branches with the same data required, it’s better to set accesses based on roles: administrators, developers, analysts, etc.
Choosing one way or combining several of them, managers can build a comprehensive yet scalable data warehouse architecture. Remember that new data/user types may appear over time and use universal classes.
Need a data warehouse? Learn how to build a data warehouse from scratch.
2. Data load and movement
Most often, data is compromised when an employee accesses it. Sometimes, hackers get quicker access to restricted areas when the packages are uploaded or downloaded. Also, workers can steal sensitive info directly. Say, in April 2019, more than 540 million Facebook private records were found on public Amazon cloud servers. It’s a bright example of poor security during data exchange between platforms.

To keep DWH privacy at a high level, answer questions related to different aspects of data movement:
- Where are the basic files stored? Who has access to these directories?
- Are there backups? How they are stored and who has access to them?
- How do you work with temporary data? Where are the query results stored?
Regardless of data type, remember to keep the same security standards. For instance, often, regular employees can make a query and get temporary tables with restricted info. It’s unacceptable.
3. Network requirements
Apart from the user and data security, we shouldn’t forget about tech stuff. Data warehouse modeling provides for designing and connecting reliable infrastructure. To make your network safe, plan how the data will flow across the organization, which ways you will use to send and receive info, and what type of encryption you will use (if any).
Our data science professionals worked with a lot of systems based on poor data warehouse architecture. One of the most common issues refers to poor scalability. Enterprises use advanced encryption methods but forget that large data packages require more processing power over time. That’s why it’s essential to plan the structure before creating the DWH.
Best practices to reach top safety
Well, now, let’s move to the exact tips & tricks! Despite serious challenges and tons of concerns to foresee, it’s definitely possible to build a reliable, safe, and powerful data warehouse. Further, we list efficient time-proven approaches to maintain perfect security. On the most basic level, these options are divided into two types: hardware of physical measures and software-based ones. We will focus on both aspects.
Hardware
Physical conditions and protection of your database may look less important than digital sides. However, they also form a crucial security level. All software decisions would be obsolete if a fraudulent employee could access the data warehouse physically and damage or steal valuable information. Hardware-focused solutions come down to three points:
- Control physical access to the warehouse. For this, advanced identification methods exist. Biometric readers, scanners, cameras, and other devices can successfully prevent unauthorized access to the servers.
- Set standardized security protocols. Ensure that all the employees (and guests if needed) know the company’s protocols. They should obey these rules all the time. Standards should be clear, understandable, and effective yet justified.
- Use only reliable hardware pieces. Old systems may fail to provide reliable security because of simple hardware issues. Servers often go down at the high loads, processors literally burn, and whole networks disable making it easier to break in.
While top-notch physical DWH privacy is often a must-have, we suggest managers calculate expenses carefully. It’s illogical to build a defense that costs several billion when the estimated losses from data leak is a few million. Still, large companies should invest in physical defense. 3 billion compromised Yahoo accounts resulted in $350 million damage, for example. Most likely, it’d be cheaper to prevent this attack.
Software
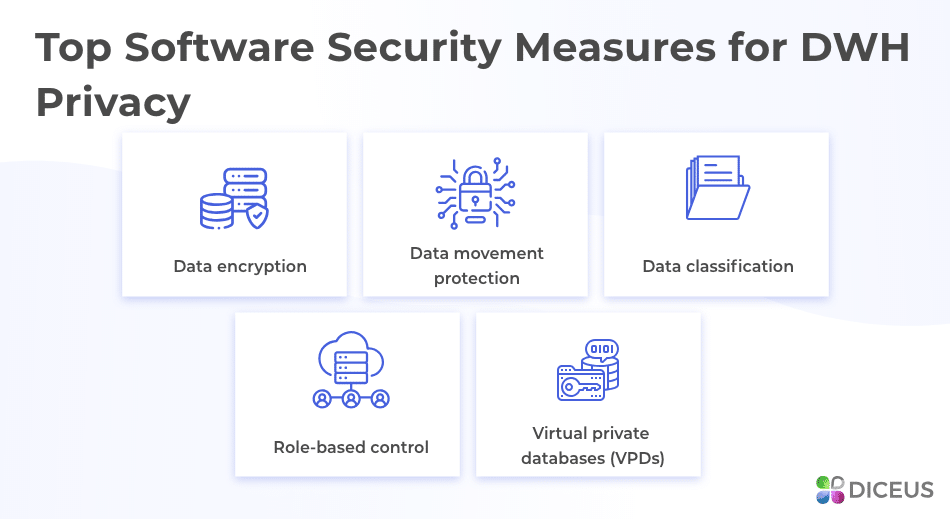
The main battle between cybersecurity specialists and hackers takes place in the digital world. Hardware acts as a basement but the software is a key factor. Let’s look at the most useful safeguards that refer to data warehouse architecture, access points, and users:
- Data encryption. The most basic protection layer provides for using encryption methods to make data unreadable for outsiders. It’s obligatory to encrypt info on transactional bases. Moreover, it’s better to use encryption in the basic DWH, too. For this, you may use AES algorithms and software certified with FIPS 140-2.
- Data movement protection. Today, a lot of data is stored in cloud systems. Surely, businesses have to move it, share with partners, copy, and so on. To protect on-the-move data, use traditional protocols, i.e. SSL and TSL. Also, try to integrate VPNs for even higher safety online.
- Data classification. According to the mentioned user accesses, all the data in warehouses should be classified. Feel free to use the method you like the most: by functions, by departments, etc. Data partitioning is required, too. It’s based on the idea of sensitivity and separates the most sensitive information from other packages.
- Role-based control. In addition to data classification, remember about user roles and privileges. Set rights for different classes so unauthorized employees couldn’t make SQL requests, create temporary tables or download data. Be sure to protect the administrator’s profiles perfectly as they can grant and disable accesses for other users.
- Virtual private databases (VPDs). These tools allow setting security measures on tables, views, words, rows, columns, and more. VPDs limit accesses dynamically and attach protection to each object instead of the whole base. With this feature, bank customers would see only their transactions and employees – only their salaries.
More information on the topic: Big data in banking: Key benefits and main challenges
Similarly to hardware protection, don’t forget to calculate expenses. If the potential damage is low, don’t invest in costly solutions – you just don’t need them. Consider reputational losses here, too. For instance, banks are interested in advanced security systems even if they don’t have a lot of sensitive data in their storage. Protected banks are more demanded by customers, obviously.
Future trends
Numerous studies describe the idea of DWH privacy. According to the analysis, the experts often talk about encryption, audit, transformation, views, multi-platform connections, and general data warehouse modeling. The majority of studies focus on extendibility and independence models while the most popular approaches include encrypted queries, UML-, and XML-based security techniques.
We can predict that old approaches like Adapted Mandatory Access control will disappear as cybersecurity professionals will introduce more efficient options. Our developers are aware of the most innovative techniques and are ready to use them for your data warehouses. Feel free to contact us if you need a consultation, upgrade, or a completely new custom DWH. Don’t wait and protect your data today!